Hi Zimbra Customers, Partners & Friends,
This blog is a short “how-to” for setting up SPF, DKIM and DMARC on Zimbra.
What is SPF?
Sender Policy Framework (SPF) helps prevent email spamming and spoofing by telling the world what servers are allowed to send email from your domain. If an email is sent from user@example.com, that email needs to be sent via a server that is allowed in the SPF DNS record published for the example.com domain. If a malicious user sends an email from an untrusted server as info@example.com, the SPF check at the recipient mail server will fail and the email will be delivered to the Spam folder.
What is DKIM?
DomainKeys Identified Mail (DKIM) can be used on top of SPF. DKIM provides a way to verify the integrity of an email message by using a digital signature. This way, if a hacker tampers with the body or subject of an email while the email travels over the Internet, the digital signature will not be valid and the recipient mail server can warn the user or put the email in a quarantine mailbox.
What is DMARC?
Domain-based Message Authentication Reporting and Conformance (DMARC) advises the receiver what should be done if an SPF or DKIM failure occurs. You can set-up DMARC in testing mode, so there are no disruptions in email delivery in the initial set-up phase. You can set-up DMARC to instruct the receiver to send a failure report back to you, so you can debug DKIM and SPF failures before setting a more strict DMARC policy.
Is this difficult to set-up?
Yes and no. Depending on your experience with DNS and Zimbra, the technical steps are easy and described below.
The difficult part is that in larger organizations, there are often many servers that send out emails, including 3rd parties like Mailchimp. You have to compile a list of all these senders, add them all to your SPF records and configure them all to use DKIM. If that isn’t possible, you have to configure these senders to relay email through a server that has DKIM/SPF set-up (such as Zimbra). In many cases, you will end up doing a combination of both.
It is probably easiest (for implementing DMARC) to keep the number of approved sending servers as low as possible. But finding out where your users are sending from can be time consuming. By putting DMARC in testing mode for a period of time and analyzing incoming failure reports, you can find out more about your users behavior before setting a strict DMARC policy.
How to Set Up SPF, DKIM and DMARC on Zimbra
Try this on a test domain first.
To have Zimbra sign outgoing messages with DKIM, you need to generate DKIM keys using the command as user zimbra:
/opt/zimbra/libexec/zmdkimkeyutil -a -d zimbratest.tk
Store the output of this command to set up in DNS later.
DKIM Data added to LDAP for domain zimbratest.tk with selector 8250020E-EF81-11EB-BB5B-4520489C3827 Public signature to enter into DNS:
8250020E-EF81-11EB-BB5B-4520489C3827._domainkey IN TXT ( "v=DKIM1; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvo1fSt7kWZkQn69KhXubeVdXg2oX0waQeCSR4zZcHccpM+kxRTYLkPVlbSJ/8Aa6Pr9LFm0+9C IJjuN9UyAeRnlYspCrN7Y8iPVB/2Vsvl6I9v1KPITB9jyY5u5ETwAu1ic2nAm4B7CsRNfgL8G6BqBQbCWU4W4onhwz3bdytMec/cgV0st+whdJTMjTflJoRvF QYcNnQRmdai"
"tTVzbnziG0k8hxFYkg0oJs5/4zdi6O6vizACwbVWckS19NsW3XPj6ppXVZ2gQYrVW4QoNnYX/ji7fBZxFonRXErCvnRrq9a743UF3kJXihAkZ7HR+dn6rXwM ZgC2dbBc8l2NxmJwIDAQAB" ) ; ----- DKIM key 8250020E-EF81-11EB-BB5B-4520489C3827 for zimbratest.tk
Next, make sure there is an email address to receive the DMARC reports:
zmprov ca postmaster@zimbratest.tk PUT-A-RANDOM-PASSWORD-HERE
Now DNS is set up. Assuming you are using a bind DNS server, add the following 3 records to your zone file (and reload bind):
@ TXT "v=spf1 a mx ~all"
_dmarc TXT "v=DMARC1; p=none; fo=1; rua=mailto:postmaster@zimbratest.tk; ruf=mailto:postmaster@zimbratest.tk" 8250020E-EF81-11EB-BB5B-4520489C3827._domainkey.zimbratest.tk. IN TXT ( "v=DKIM1; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvo1fSt7kWZkQn69KhXubeVdXg2oX0waQeCSR4zZcHccpM+kxRTYLkPVlbSJ/8Aa6Pr9LFm0+9C IJjuN9UyAeRnlYspCrN7Y8iPVB/2Vsvl6I9v1KPITB9jyY5u5ETwAu1ic2nAm4B7CsRNfgL8G6BqBQbCWU4W4onhwz3bdytMec/cgV0st+whdJTMjTflJoRvF QYcNnQRmdai"
"tTVzbnziG0k8hxFYkg0oJs5/4zdi6O6vizACwbVWckS19NsW3XPj6ppXVZ2gQYrVW4QoNnYX/ji7fBZxFonRXErCvnRrq9a743UF3kJXihAkZ7HR+dn6rXwM ZgC2dbBc8l2NxmJwIDAQAB" ) ; ----- DKIM key 8250020E-EF81-11EB-BB5B-4520489C3827 for zimbratest.tk
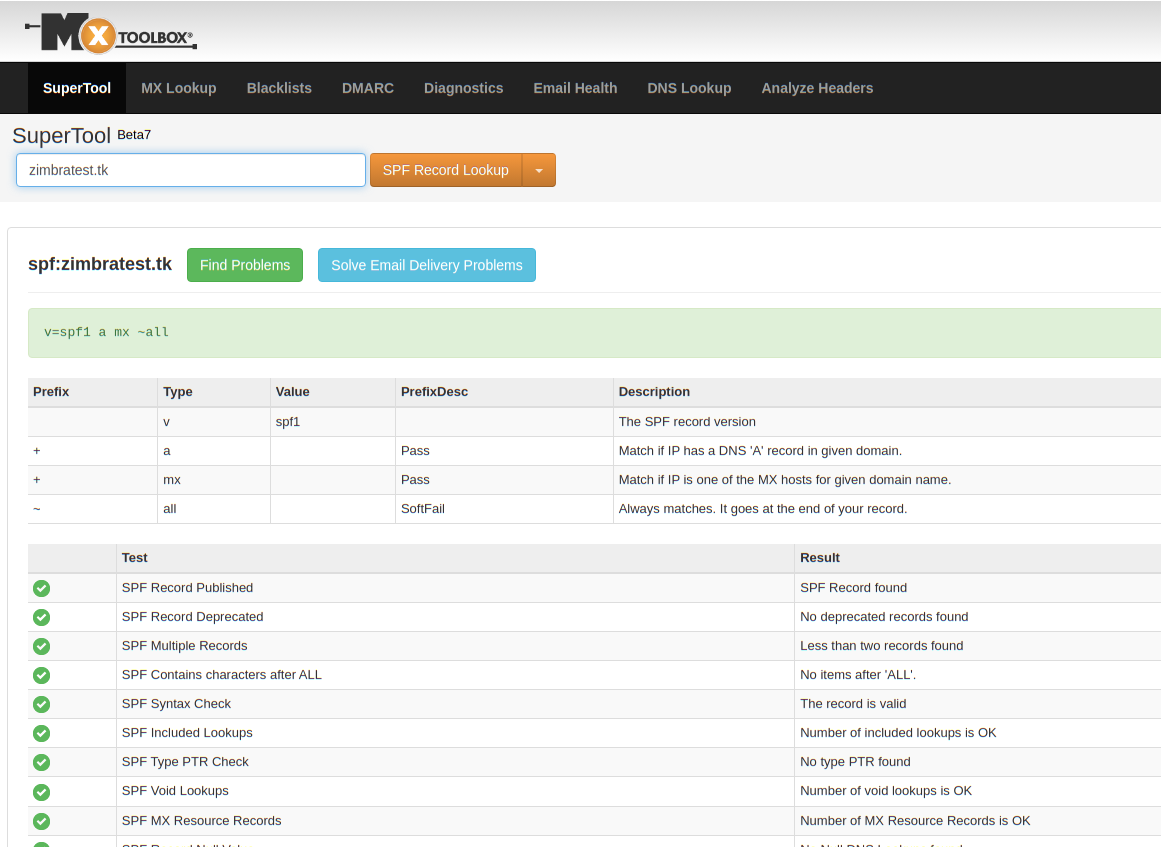
The SPF record v=spf1 a mx ~all tells the world the version of SPF used and allows email to be sent from the servers in our A and MX records, which is your website and mail server. You can also add other IP addresses or ranges (see the references below for more information). The ~all tells the world to put all email that is coming from other origins into the Spam folder.
Test your SPF record via an online tool such as https://mxtoolbox.com/SuperTool.aspx?action=spf to be sure it is configured correctly.
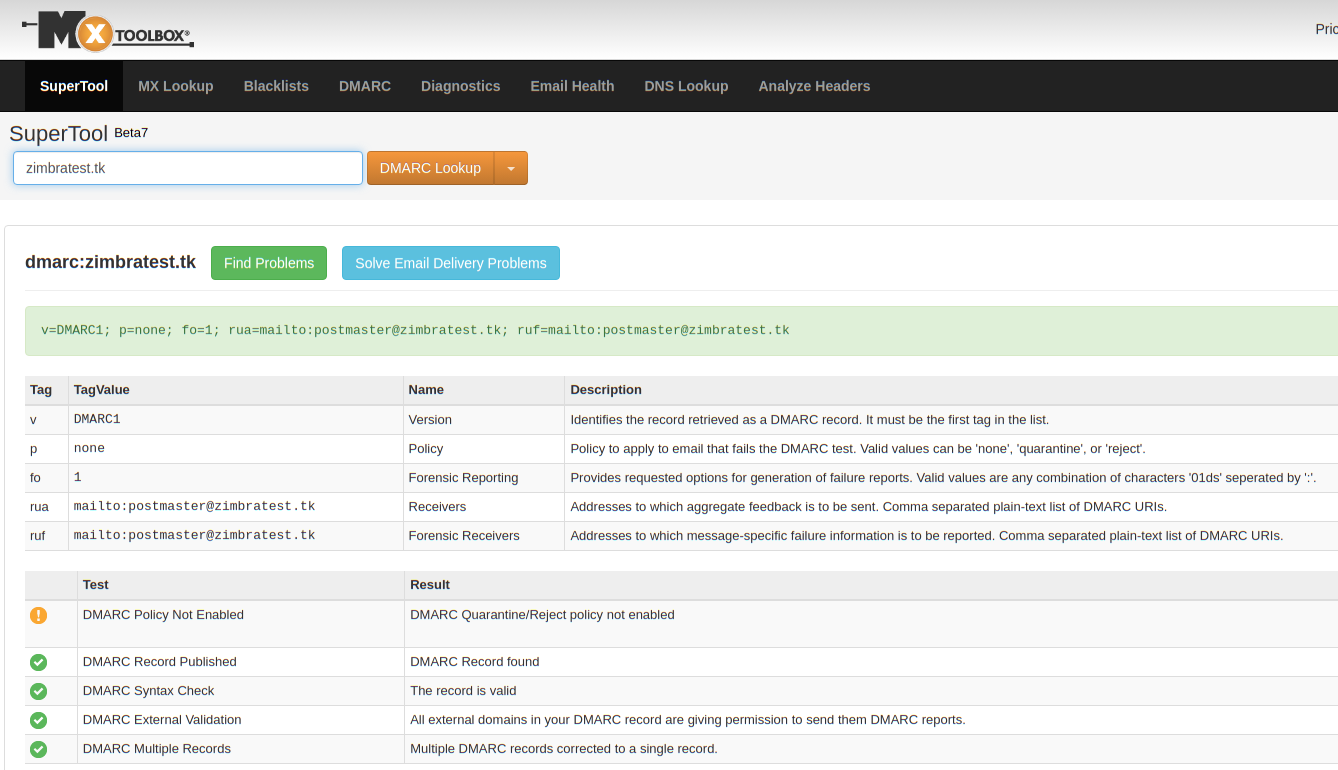
The DMARC record v=DMARC1; p=none; fo=1; rua=mailto:postmaster@zimbratest.tk; ruf=mailto:postmaster@zimbratest.tk tells the world what version of DMARC you’re using. The p=none indicates testing mode. The email will be processed as if we are not using DMARC, but failure reports are sent to the addresses defined in rua and ruf.
Test your DMARC record via an online tool such as https://mxtoolbox.com/SuperTool.aspx? action=dmarc to be sure it is configured correctly.
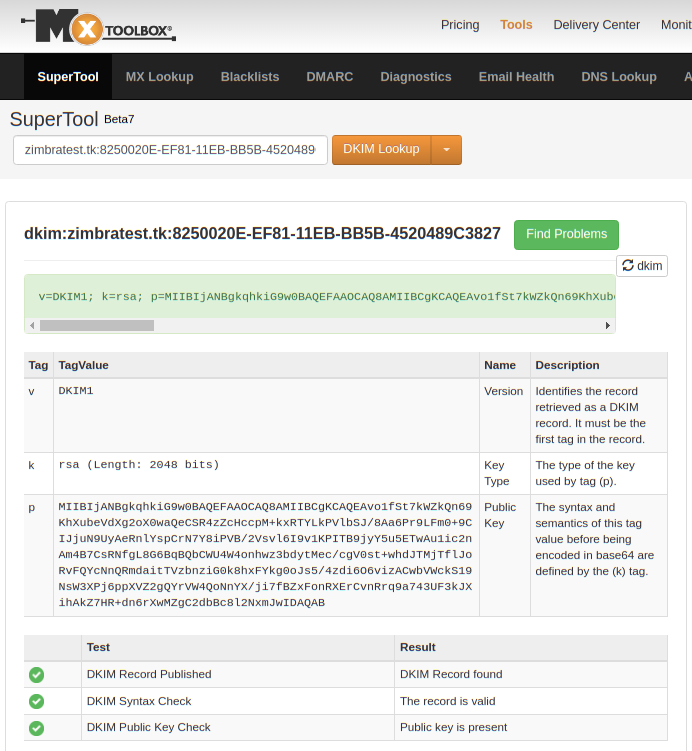
The DKIM record is a copy-paste from the output of the zmdkimkeyutil command, we only need to add .zimbratest.tk in case bind DNS server is used. You can check the DKIM record via https://mxtoolbox.com/SuperTool.aspx?action=dkim and do a lookup for zimbratest.tk:8250020E- EF81-11EB-BB5B-4520489C3827
Now you can do one last test on Zimbra:
[zimbra@mind root]$ /opt/zimbra/common/sbin/opendkim-testkey -d zimbratest.tk -s 8250020E-EF81-11EB-BB5B-4520489C3827 -x /opt/zimbra/conf/opendkim.conf
opendkim-testkey: '8250020E-EF81-11EB-BB5B-4520489C3827._domainkey.zimbratest.tk' query failed
[zimbra@mind root]$ /opt/zimbra/common/sbin/opendkim-testkey -d zimbratest.tk -s 8250020E-EF81-11EB-BB5B-4520489C3827 -x /opt/zimbra/conf/opendkim.conf
If there are no errors reported by the command, you can enable the DKIM signing by running as user zimbra:
zmprov ms `zmhostname` +zimbraServiceEnabled opendkim
Do a real test
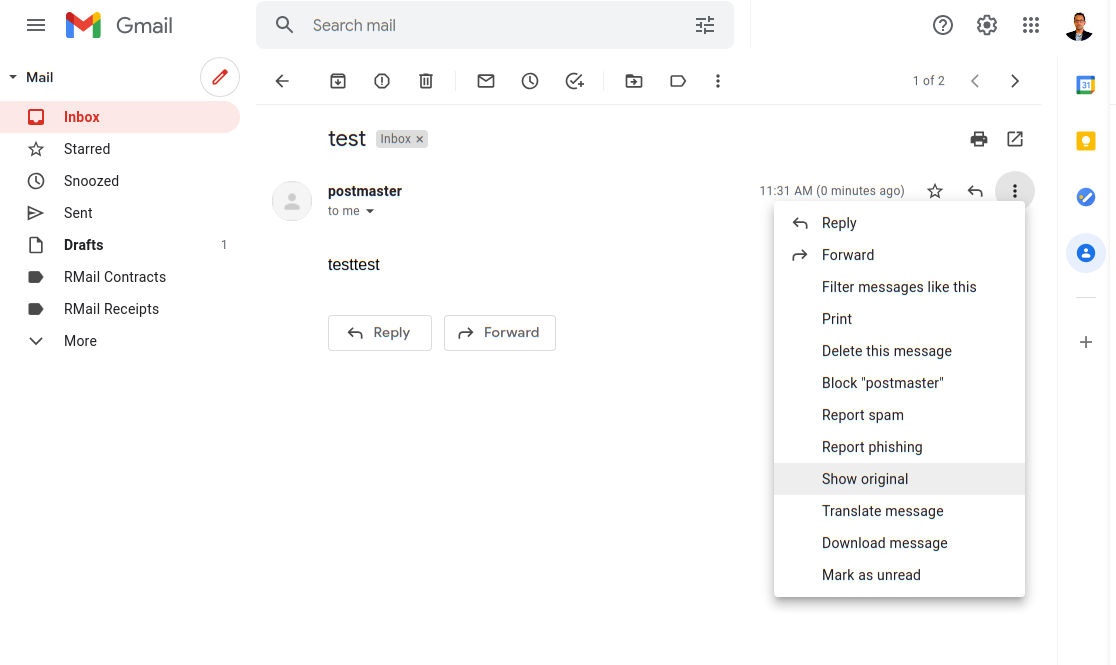
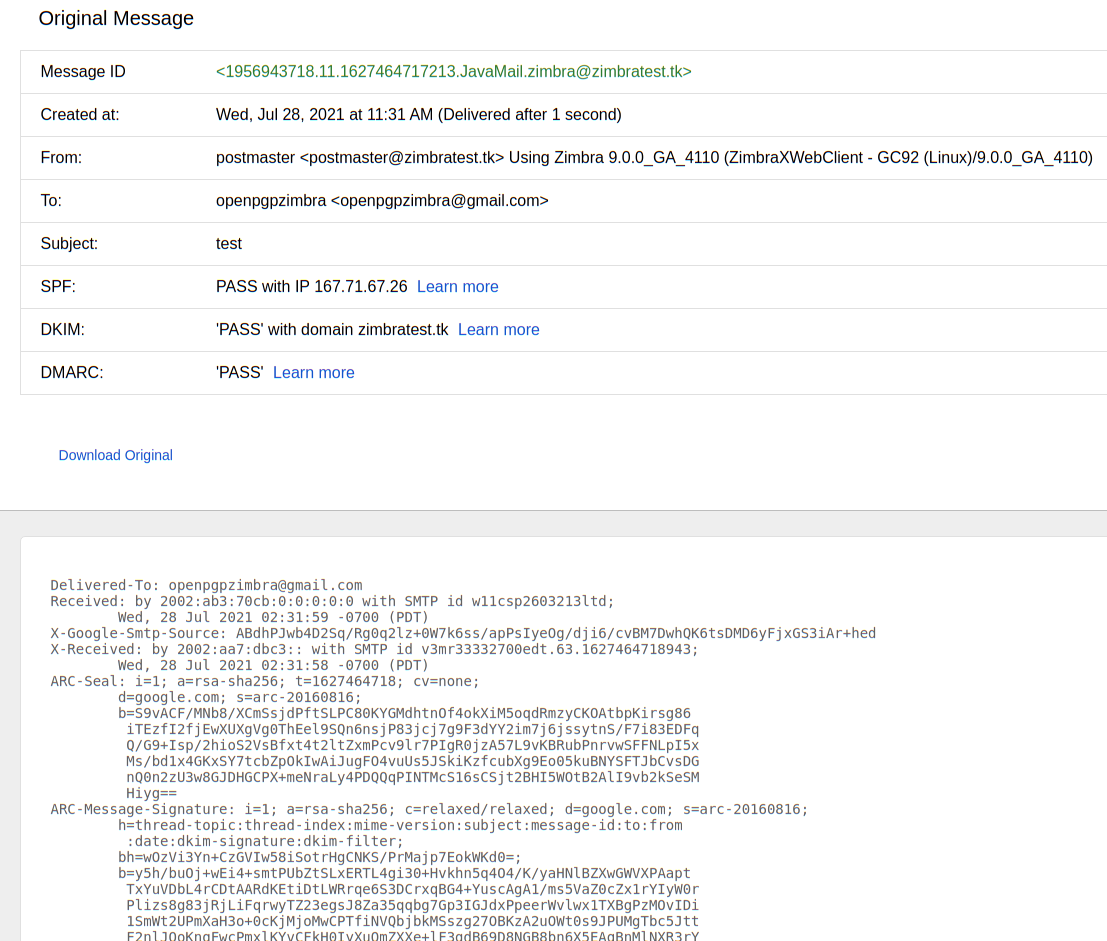
The easiest way to test your configuration is to send an email to a 3rd party like Gmail.
Click the Show Original menu option.
You should see PASS at SPF, DKIM and DMARC.
Periodically check the DMARC reports that should come to the address configured in the DMARC record. If you feel you are ready update your DMARC record to:
_dmarc TXT "v=DMARC1; p=quarantine; fo=1; rua=mailto:postmaster@zimbratest.tk; ruf=mailto:postmaster@zimbratest.tk"
Gotchas
Please note that enabling DKIM on Zimbra means you cannot change the content of an email after it has been DKIM signed. This shouldn’t happen on a default installation, but it can happen if you use custom milters, domain disclaimers, amavis customizations, etc. In some cases you can change the order so the DKIM signing is done last. Or you have to strip and re-do the DKIM signing. If you have trouble with DKIM failing, try this tool https://www.appmaildev.com/en/dkimfile.
References and tools
• https://wiki.zimbra.com/wiki/Configuring_for_DKIM_Signing
• https://wiki.zimbra.com/wiki/Best_Practices_on_Email_Protection:_SPF,_DKIM_and_DMARC
• https://www.appmaildev.com/en/dkimfile (tool for checking DKIM digital signature)
• https://mxtoolbox.com/DMARC.aspx
• https://www.dmarcanalyzer.com/spf/
• https://www.sparkpost.com/resources/email-explained/dkim-domainkeys-identified-mail/
• https://www.dmarcanalyzer.com/dmarc/
Thanks,
Your Zimbra Team

DMARC reports can be cryptic to read, and with forensic reporting turned on as Barry recommends (we agree), they can be voluminous. We recommend our customers use a DMARC reporting service to receive the reports and provide you with a pretty dashboard. Mission Critical Email uses dmarcian.com, but there others (Google search for “dmarc analysis free”)
Thank you for posting this insight on SPF, DKIM, and DMARC. Keep up this important work.
It’s usually advised to have each “SaaS”-service relegated to its own subdomain, because there is also a limit on how many entries an SPF or DKIM record can actually have.
And it’s better to have a subdomain blacklisted than the main domain, in case something goes wrong.
HI
can You separate 3 records I have to add to my DNS?
I see 4 lines and I have problem to understand it.
I assume you are having problems adding the DKIM key. In Bind DNS server, this record is split over multiple lines.
However if you use a different DNS server, you can probably put the entire DKIM key in one line. By removing the quotes (“) and newline’s. So it would become:
8250020E-EF81-11EB-BB5B-4520489C3827._domainkey IN TXT "v=DKIM1; k=rsa;p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvo1fSt7kWZkQn69KhXubeVdXg2oX0waQeCSR4zZcHccpM+kxRTYLkPVlbSJ/8Aa6Pr9LFm0+9C IJjuN9UyAeRnlYspCrN7Y8iPVB/2Vsvl6I9v1KPITB9jyY5u5ETwAu1ic2nAm4B7CsRNfgL8G6BqBQbCWU4W4onhwz3bdytMec/cgV0st+whdJTMjTflJoRvF QYcNnQRmdaitTVzbnziG0k8hxFYkg0oJs5/4zdi6O6vizACwbVWckS19NsW3XPj6ppXVZ2gQYrVW4QoNnYX/ji7fBZxFonRXErCvnRrq9a743UF3kJXihAkZ7HR+dn6rXwM ZgC2dbBc8l2NxmJwIDAQAB"