Hello Zimbra Customers, Partners & Friends,
In today’s blog, I’ll show you how to add an external email warning message in Zimbra when receiving an email from an external domain. This is done using a Sieve filter, and it can be enabled per account, COS, domain and server.
First, create /tmp/myfilters
su - zimbra nano /tmp/myfilters
With the following contents:
require ["fileinto", "reject", "tag", "flag", "editheader", "variables"];
# add an external domain header to all email not coming from our own domains
if allof(
not address :domain :is ["from"] ["example.com"],
not header :contains "Subject" ["[External Email]"]
)
{
addheader "X-External-Domain" "This Message originated outside of mind.";
# Match the entire subject ...
if header :matches "Subject" "*" {
# ... to get it in a match group that can then be stored in a variable:
set "subject" "${1}";
}
# We can't "replace" a header, but we can delete (all instances of) it and
# re-add (a single instance of) it:
deleteheader "Subject";
# Append/prepend as you see fit
addheader :last "Subject" "[External Email] ${subject}";
# Note that the header is added ":last" (so it won't appear before possible
# "Received" headers).
}
Replace example.com with your Zimbra domain name. You can also add additional trusted domains where you don’t want the external email warning to be displayed using:
not address :domain :is ["from"] ["example.com","supermodel.com","gamer.tech"],
Enable it on a test account using
zmprov mc default zimbraSieveEditHeaderEnabled TRUE cat /tmp/myfilters |xargs -0 zmprov ma test@example.com zimbraAdminSieveScriptBefore
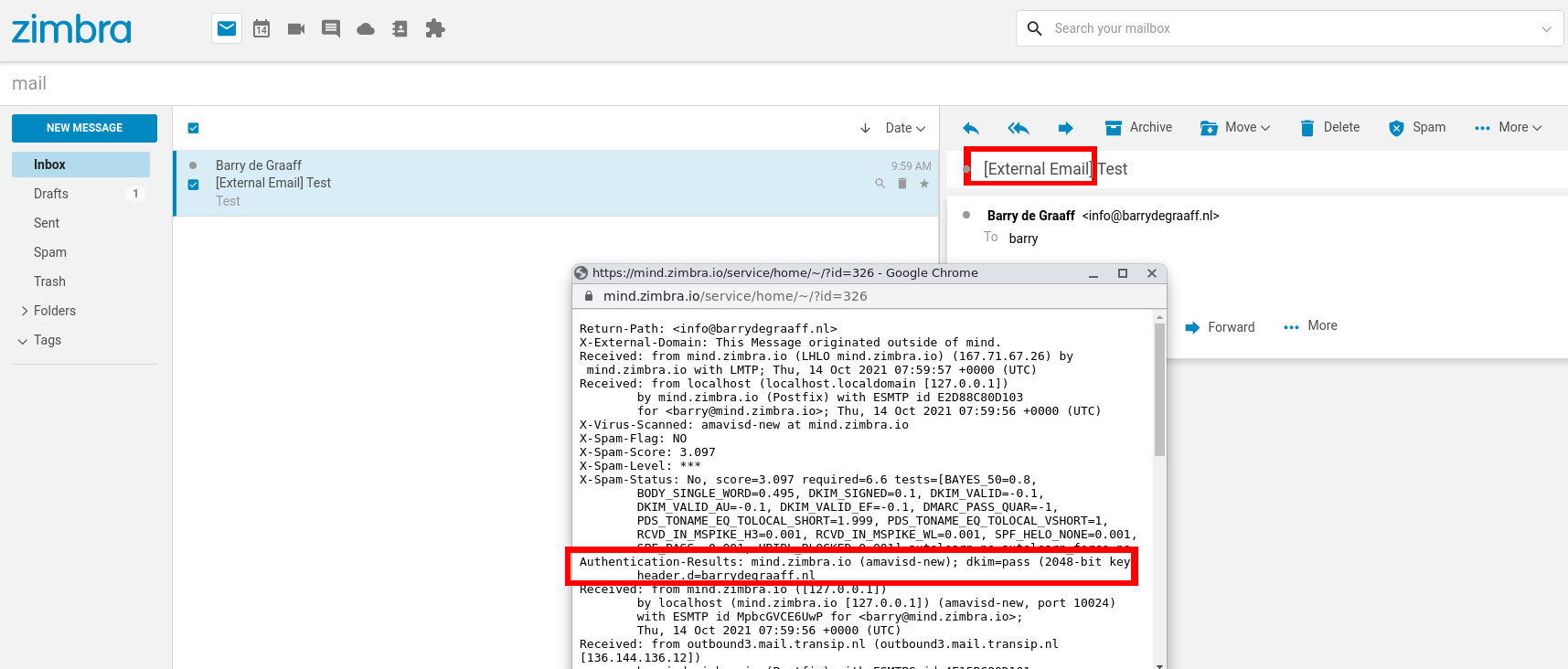
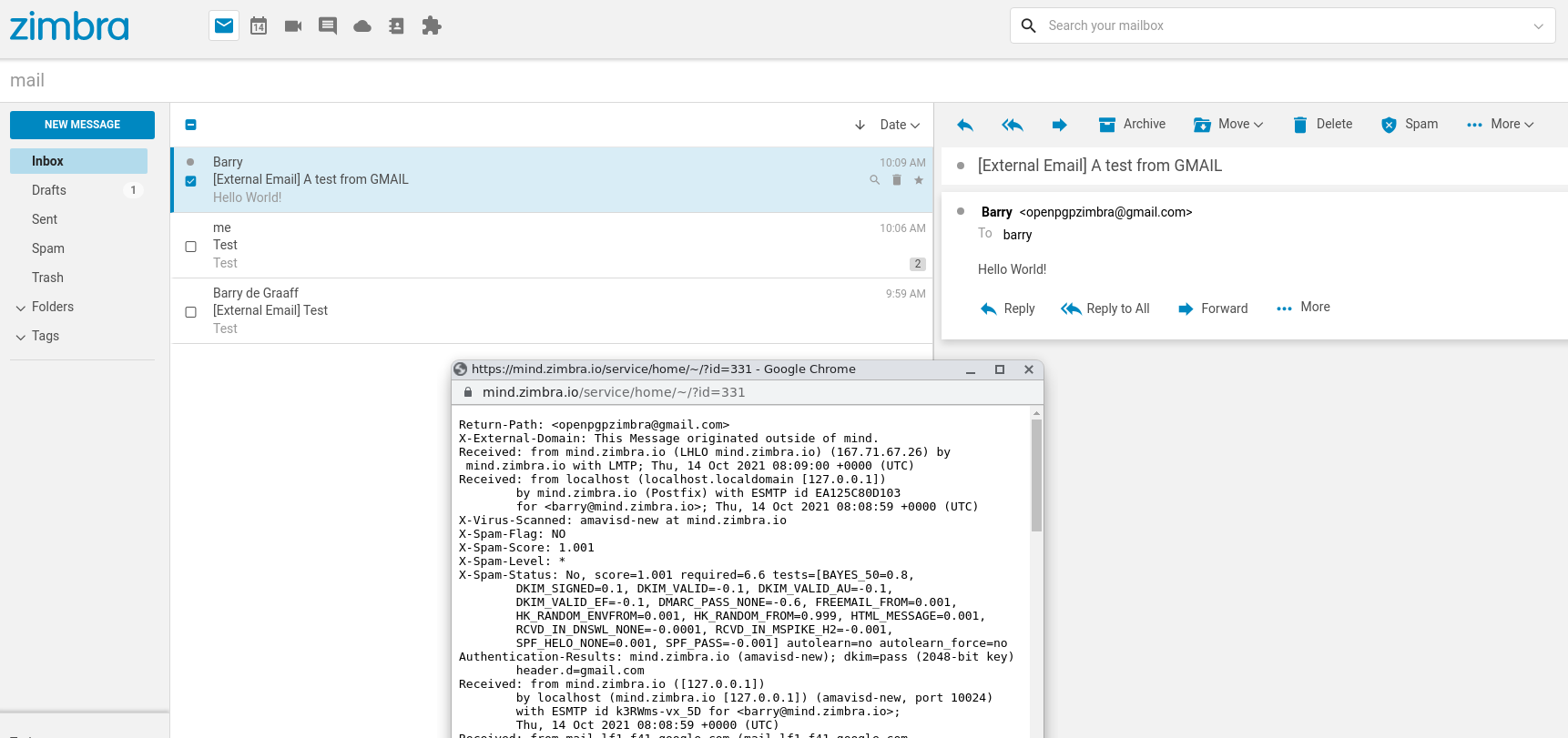
Here are some example screenshots when receiving email from outside/external domains:
How to deal with user defined forwarded email
A user can configure Zimbra to forward their email to another user. To
be able to make a Sieve filter rule that can tell the difference between
a user-configured forwarded email and a mail sent manually by the user
you can enable the X-Authenticated-User header:
sudo su zimbra zmprov mcf zimbraSmtpSendAddAuthenticatedUser TRUE zmprov mcf zimbraMtaSmtpdSaslAuthenticatedHeader yes zmcontrol restart
Going forward, manually sent email from the user will have the
X-Authenticated-User header, and forwarded email will NOT have the
header. You can write a Sieve filter for the existence of a header as
follows:
if allof(
address :is :domain ["from", "sender"] ["example.com","supermodel.com","gamer.tech"],
not exists ["X-Authenticated-User"]
)
{
# do something here
stop;
}
Gotchas
- Modifying the message like this will break DKIM. Users can re-validate DKIM manually after it was verified and the subject was changed, but not many people do this.
- This is not a protection against spoofing. You have to reject email with a FROM domain that comes from untrusted locations, but that should’ve been done anyway.
- In a multi-tenant environment, it would be best to configure this on the domain. Even if domains are on the same environment, they may be external to one another.
Further reading
Stay safe,
Your Zimbra Team


Hello Barry, i have a some question. I add this script a user incoming mail added to subject External tag everytinh is fine, but i reply mail and again write a answer this time mail added second External Tag, do yu have a solution this issue
Thanks, I have added a check to the Sieve script so that it will not put duplicates of the external email warning!
Thank you for quick reply. Last question, i need a add few domain how should I use it?
not address :domain :is ["from"] ["example.com","supermodel.com","gamer.tech"],
Thank you Barry.
The External should be added if the mail is inbound, from the Internet. Is it possible to look for Received line or X-Originating-IP to determine this?
Here is the code for getting X-Originating-IP in Sieve
if header :is "X-Originating-IP" "put-an-ip-here" {#do something here
stop;
}
Barry, Thank you for this blog information! It is very useful! Can you tell me if it is possible to apply the AdminSieveScripts to user-specified forwarding address accounts or any forwarded accounts in Zimbra?
Hello Will,
Not directly, but you could consider enabling the X-Authenticated-User header, via:
sudo su zimbra -
zmprov mcf zimbraSmtpSendAddAuthenticatedUser TRUE"
zmprov mcf zimbraMtaSmtpdSaslAuthenticatedHeader yes
zmcontrol restart
Then when the user is sending an email the X-Authenticated-User header is added to all outgoing email. However… for forwarded email the header will not be set. That way you should be able to tell the difference between a manually sent email and a forwarded one.