In this article you will learn:
- How to prevent users from choosing common passwords
- How to add leaked passwords to the list of passwords to reject
Enabled the Reject Common Passwords feature
You can enable the Zimbra Reject Common Passwords on a per account basis or for an entire Class Of Service (CoS). To enable the feature for the default CoS via the command line you can run the following command as the OS user zimbra:
zmprov mc default zimbraPasswordBlockCommonEnabled TRUE
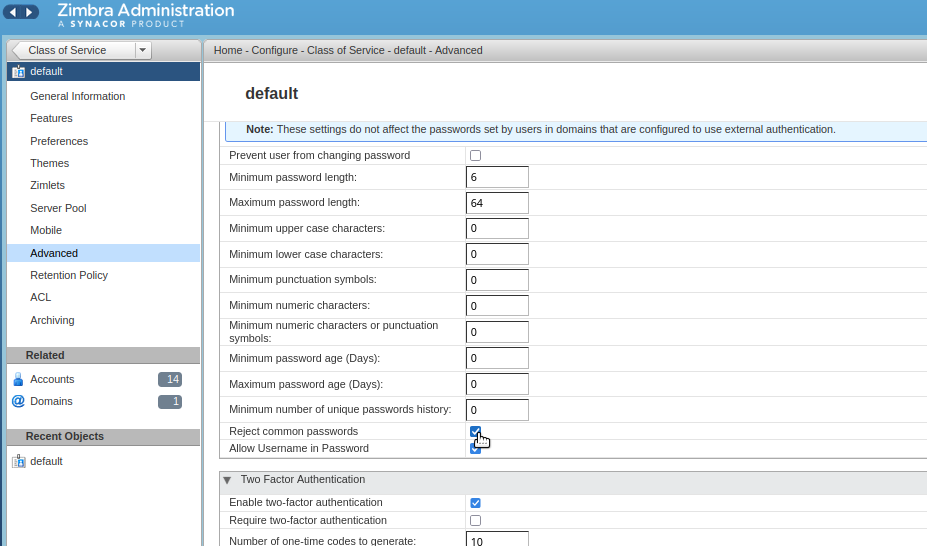
You can also enable the feature via the Admin Console web UI. Go to Configure → Class of Service → default → Advanced and check Reject common passwords option. Don’t forget to click Save.
Adding leaked passwords to the list of common passwords
The common password list is sourced from the https://github.com/danielmiessler/SecLists and is stored in the following Zimbra configuration file:
/opt/zimbra/conf/common-passwords.txt
If you want to add additional (leaked) passwords to the list of common passwords to reject them, you can add each password on a new line in the common-passwords.txt file. For example add the password:
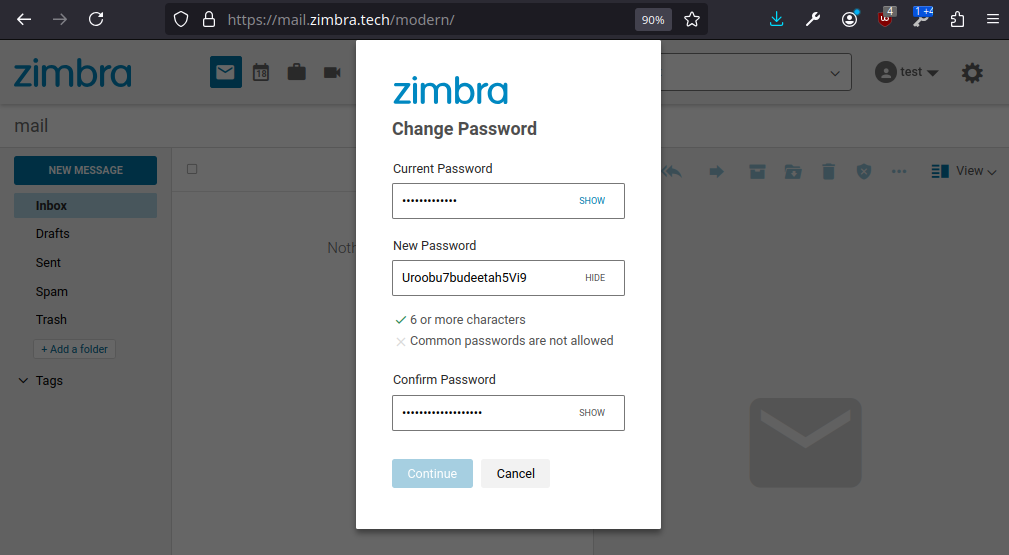
Uroobu7budeetah5Vi9
After making changes to the common-passwords.txt file restart Zimbra mailbox via the command line as the OS user zimbra:
zmmailboxdctl restart
Change password
Gotchas
- The contents of the common-passwords.txt file does not affect existing passwords.
- Administrators setting passwords from the command line will receive a warning, but can set common passwords if they desire:
zmprov sp test@zimbra.tech 123456 Password violation: account=test@zimbra.tech, violation=invalid password: too common. Password is set successfully.

Comments are closed.